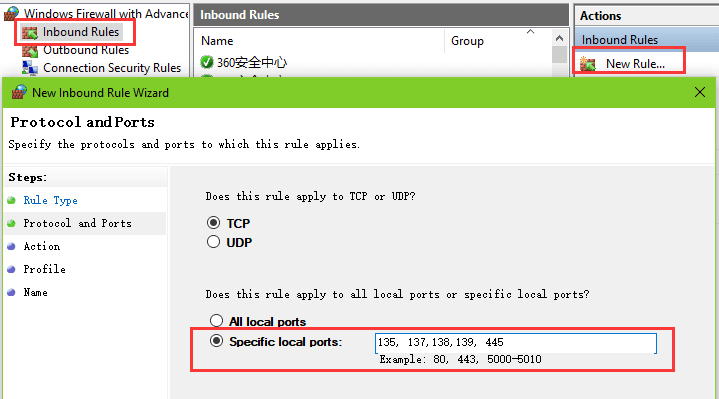
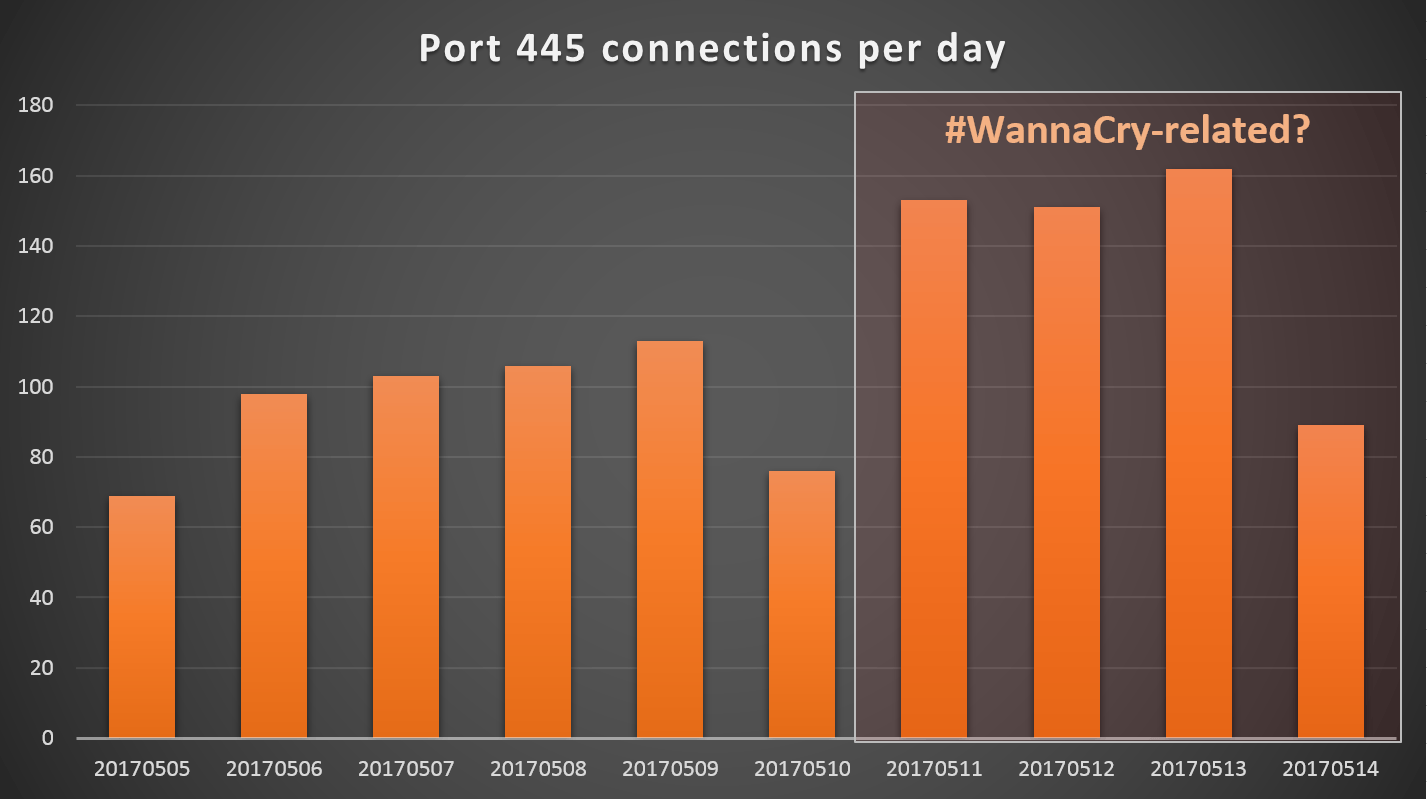
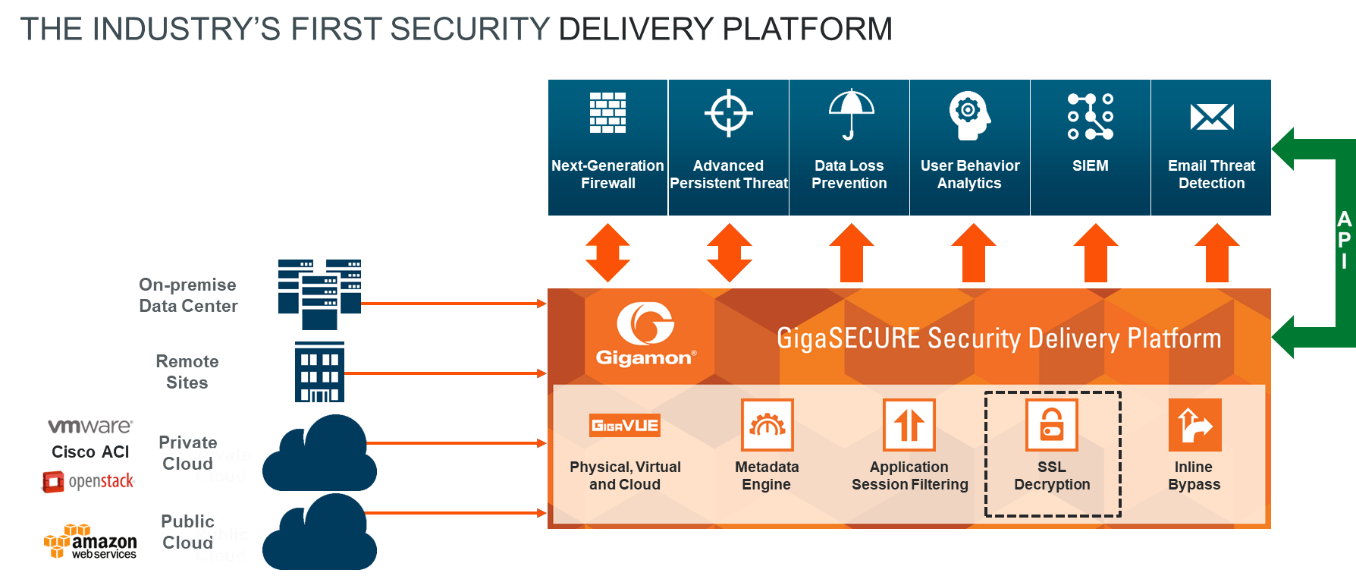
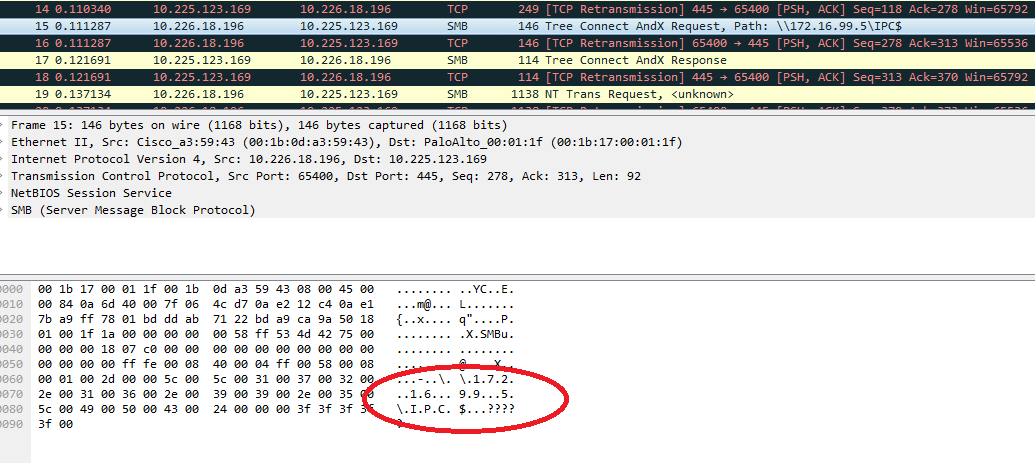
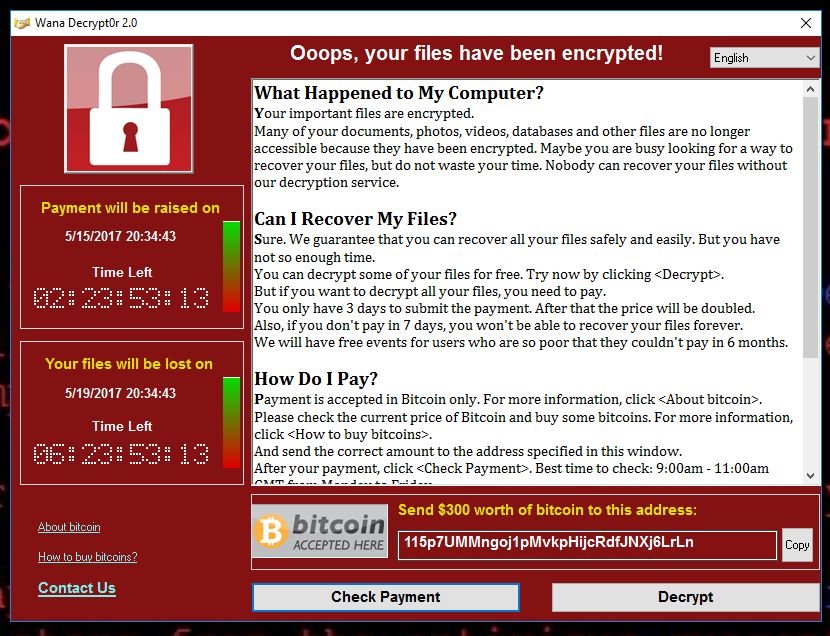
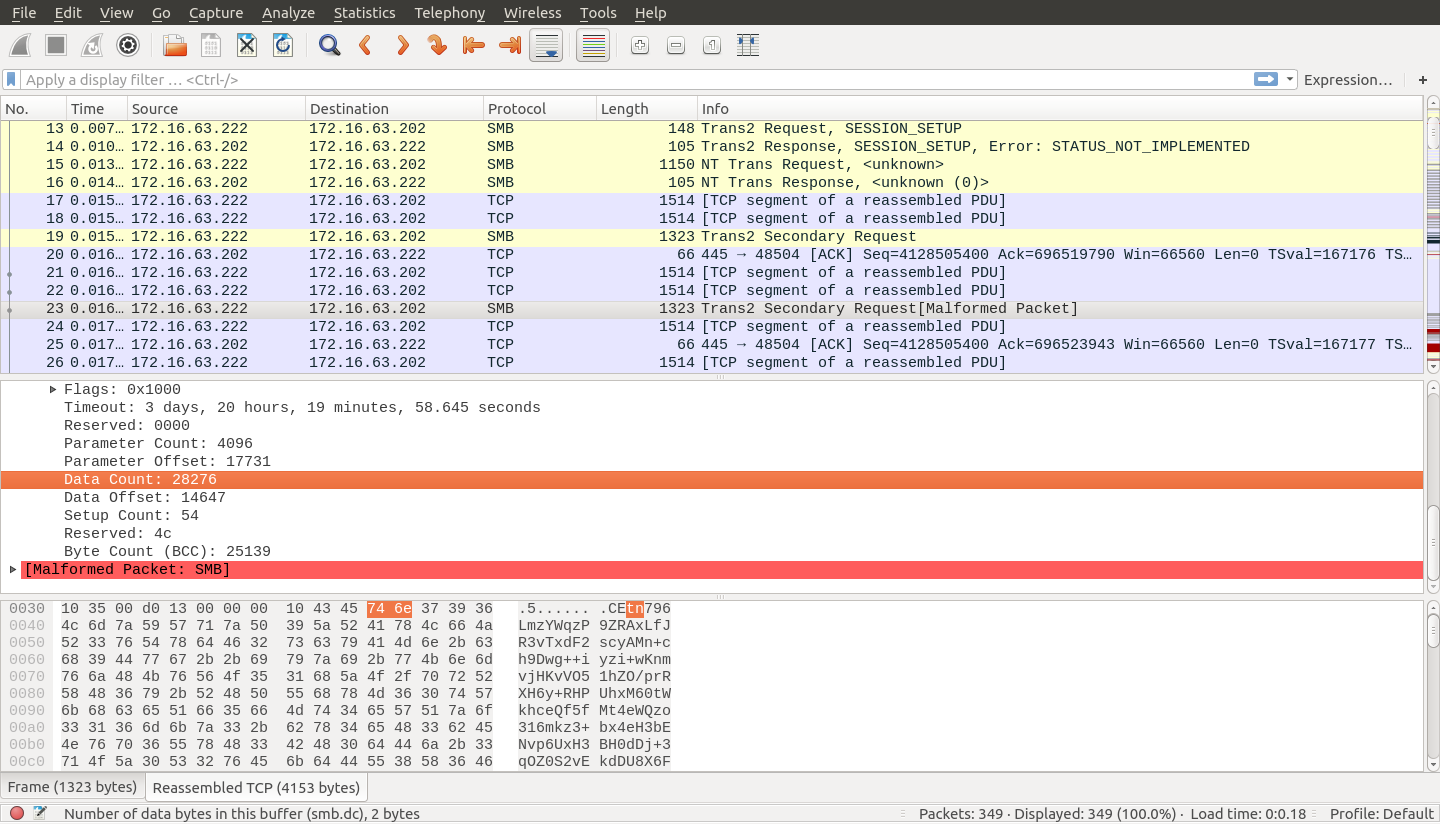
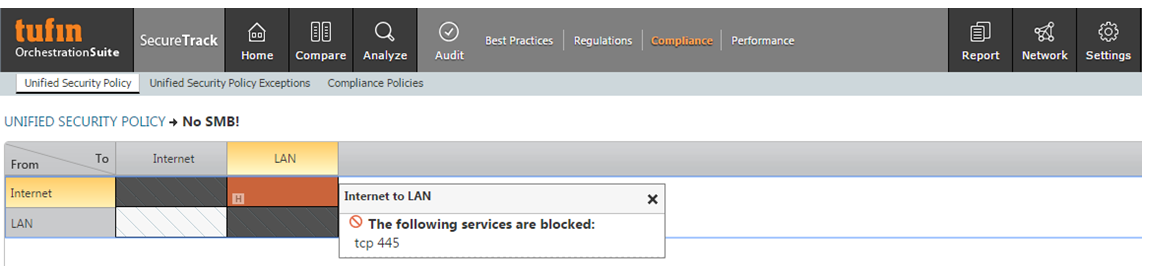
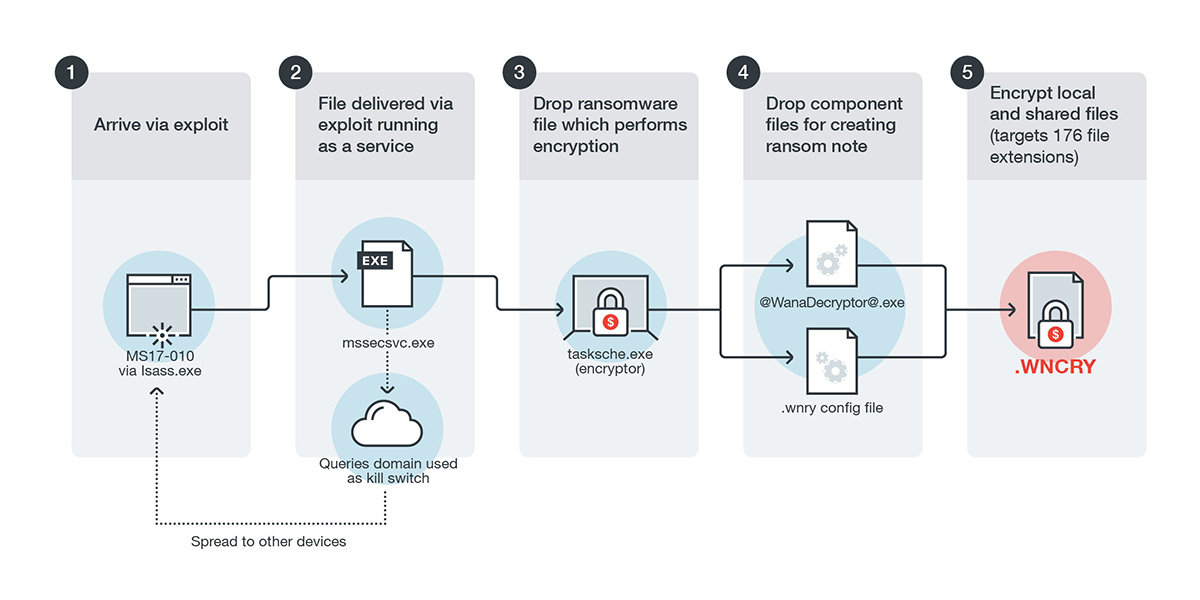
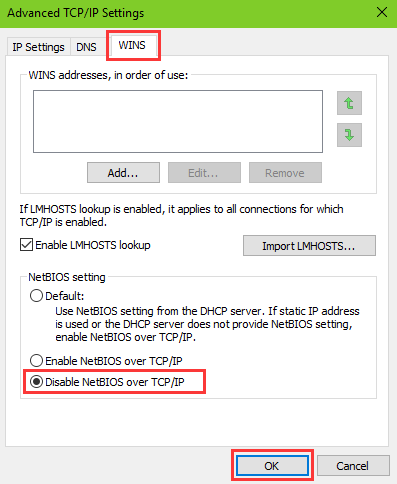
WannaCry Update: Vulnerable SMB Shares Are Widely Deployed And People Are Scanning For Them (Port 445 Exploit) | Rapid7 Blog
5.5 Million Devices Operating with WannaCry Port Open | Data Center Knowledge | News and analysis for the data center industry